Welcome to my blog. I am a computer technician, and friends around me often ask me to help them solve some computer problems. The problem mostly encountered is the core file of the operating system is damaged, resulting in the abnormal system running. In fact, the problem is generally caused by the installation of some malicious software, or a virus has implanted.
Why can't the new or variant virus still be completely eliminated, since there are so much antivirus software now with a rapidly updated virus database?
This is because most of the anti-virus software uses traditional anti-virus technology, with "static signature" to determine whether a file is a virus.
What is a static signature?
The static signature is, in a known virus file, by extracting some unique code with malicious behavior, and then combining the code together, to form a signature. Any file containing this signature code, is considered as a harmful file.
The static signature has a big flaw which is it is difficult to detect variants of the virus, or the latest unknown virus. Of course, the static signature also has the advantage that the detection speed is fast and the false detection rate is low.
However, I think the most important thing for good antivirus software, is to check out the unknown new or variable virus. Every day a large number of new viruses appear on the Internet, and it is most important on how to prevent these viruses.
Why develop "T21" system?
I was also a victim. A few years ago my computer was infected with a Trojan virus, resulting in fraudulent using of my credit card, and so far my friends around also suffer from illegally fraudulent using of their personal credit card sometimes. I hate those guys who make the virus, so I think it is necessary to do something to prevent these unknown viruses.
It's time to warn guys who do bad things!
I intend to develop a kind of system (T21) based on "behavior" to determine and prevent the unknown new virus.
What is the "behavior-based" detection method?
The "Behavior-based" detection method, completely different from the traditional static signature method, is a new detection strategy.
We first list some common behaviors, each one of which is given a numerical value to indicate the severity level, and the higher value it has, the more serious the level is:
1. Often gather together with the bad people (Severity level: 5 points)
2. Be mischievous to others (Severity level: 2 points)
3. Steal from others (Severity level: 30 points)
4. Beat others (Severity level: 19 points)
5. Destroy public facilities (Severity level: 7 points)
6. Murder (Severity level: 80 points)
7. Lie and cheat (Severity level: 6 points)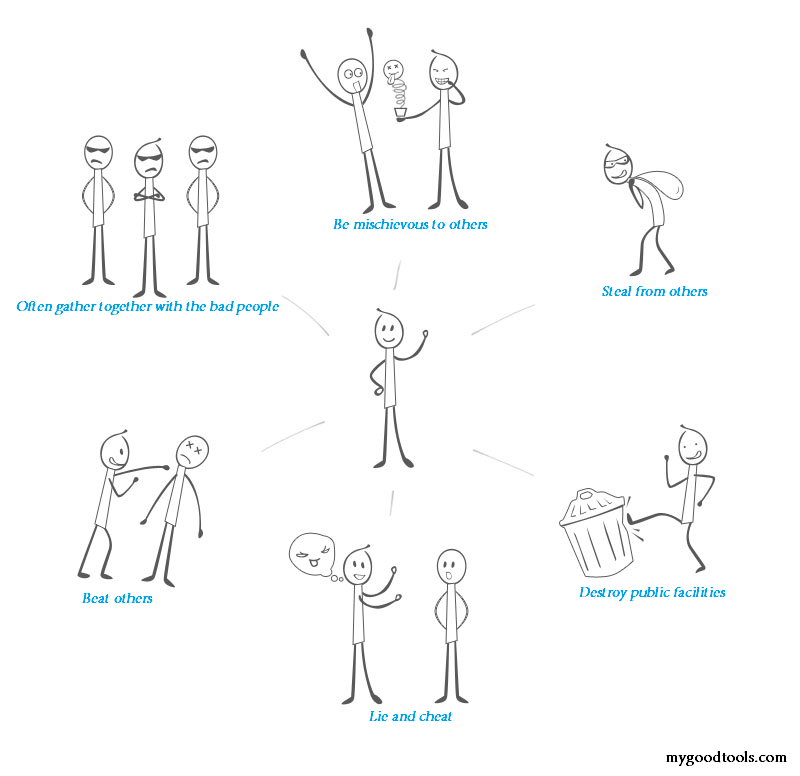
The example begins: Suppose we are in real life, to judge whether a person A is bad; first of all we need to carefully observe his behavior, and then according to his multiple behaviors we conduct a comprehensive analysis, in order to accurately determine whether the character A is bad.
Assuming that the behavior of the character A coincides with the first item, that is, often gathering together with the bad people, it can only show that A has this behavior, but cannot determine A is bad, for it is possible A just played with friends, and did not do bad things. However, as A meets the first behavior item, A's behavior score is 5 points, and because the behavior score is not very high, A is judged as: normal ordinary people.
If A has other bad behaviors, such as behavior 2 (Severity level: 2 points), behavior 3 (Severity level: 30 points), then A's behavior score is: 5+2+30=37 points. A still cannot be considered to be bad, because A's current bad behavior is not very serious, but his behavior score is higher than the average person, so A is judged as: not very popular people.
Next, if A has other bad behaviors, such as behavior 4 (Severity level: 19 points), behavior 5 (Severity level: 7 points), behavior 7 (Severity level: 6 points), now A's behavior scores is: 37+19+7+6=69 points. At this time the score reaches 69 points which is a little high, but this value has not yet reached the critical value of being judged as a bad guy, so A is judged as: disgusted people who should be estranged.
If A has a lot of other bad behaviors, then his behavior score will continue to accumulate, and once the score exceeds a set value, then A will be judged as: a bad guy.
So far, you must have understood, right? This is the active defense strategy to determine based on "behavior" standard.
So according to this principle, you can consider an executable file as a "person", and then according to various acts of the "people" to comprehensively determine, whether the executable file is a normal file.
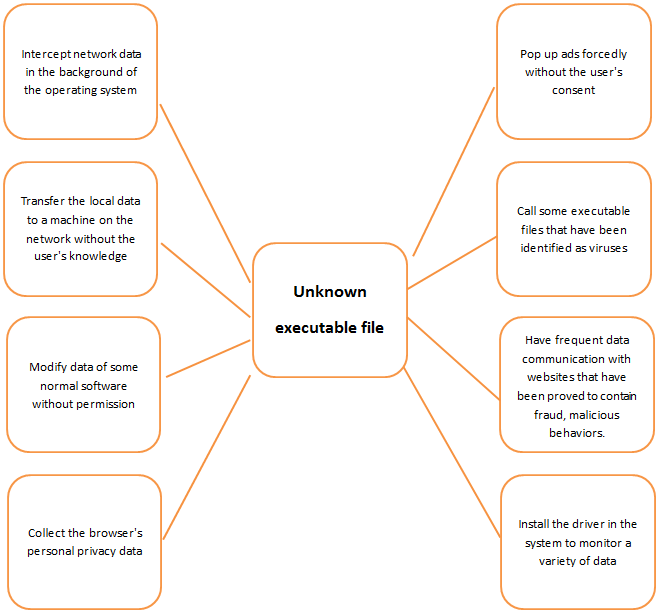
In the computer, there are a lot of behaviors that are not friendly. For example:
1. Intercept network data in the background of the operating system
2. Transfer the local data to a machine on the network without the user's consent or without the user's knowledge
3. Modify data of some normal software without permission
4. Collect the browser's personal privacy data
5. Pop up ads forcedly without the user's consent
6. Call some executable files that have been identified as viruses
7. Have frequent data communication with websites that have been proved to contain fraud, malicious behaviors.
8. Install the driver in the system to monitor a variety of data
... and other various unfriendly behaviors
By analyzing the code of an executable file, and establishing a virtual environment to simulate the operation of the executable file, in the course of the operation, the various bad behaviors will have accumulated scores. According to the final score, a file may be defined as one of the following types:
1. Normal file
2. File with suspicious behavior
3. Dangerous file with obvious malicious behavior
Why should the unknown file be uploaded to the server, and why not do a client for this function? How does the server analyze unknown files?
1. The server has a lot of data, as the data is too large, there is no way to integrate into the client.
2. The server will read all the code in the executable file into a virtual environment, then run the code of the executable file and rate the various actions of the file. This process requires a lot of hardware resources, while most of the personal computer configuration cannot meet this requirement.
I personally think that this "behavior-based" detection approach is a step forward, and a more secure solution that can deal with a variety of unknown new viruses.
I would like to share this idea, and wish computer security technical staff who read this, think about this direction.
Later, if I have a better idea, I will continue to share it, hoping to contribute to the cause of computer security, so that everyone is away from the computer virus, no longer suffering a variety of losses.
Why does the "T21" system apply the "behavior" based detection strategy, while also continuing to use the static signature method?
I said before, although the static signature cannot detect a new unknown virus, it has a very obvious advantage which is: fast detection speed at very low false detection rate, for the known virus file.
Therefore, the use of static signatures as an auxiliary detection approach can save a lot of time, but also reduce a lot of burden for the server.
Why can't the new or variant virus still be completely eliminated, since there are so much antivirus software now with a rapidly updated virus database?
This is because most of the anti-virus software uses traditional anti-virus technology, with "static signature" to determine whether a file is a virus.
What is a static signature?
The static signature is, in a known virus file, by extracting some unique code with malicious behavior, and then combining the code together, to form a signature. Any file containing this signature code, is considered as a harmful file.
The static signature has a big flaw which is it is difficult to detect variants of the virus, or the latest unknown virus. Of course, the static signature also has the advantage that the detection speed is fast and the false detection rate is low.
However, I think the most important thing for good antivirus software, is to check out the unknown new or variable virus. Every day a large number of new viruses appear on the Internet, and it is most important on how to prevent these viruses.
Why develop "T21" system?
I was also a victim. A few years ago my computer was infected with a Trojan virus, resulting in fraudulent using of my credit card, and so far my friends around also suffer from illegally fraudulent using of their personal credit card sometimes. I hate those guys who make the virus, so I think it is necessary to do something to prevent these unknown viruses.
It's time to warn guys who do bad things!
I intend to develop a kind of system (T21) based on "behavior" to determine and prevent the unknown new virus.
What is the "behavior-based" detection method?
The "Behavior-based" detection method, completely different from the traditional static signature method, is a new detection strategy.
We first list some common behaviors, each one of which is given a numerical value to indicate the severity level, and the higher value it has, the more serious the level is:
1. Often gather together with the bad people (Severity level: 5 points)
2. Be mischievous to others (Severity level: 2 points)
3. Steal from others (Severity level: 30 points)
4. Beat others (Severity level: 19 points)
5. Destroy public facilities (Severity level: 7 points)
6. Murder (Severity level: 80 points)
7. Lie and cheat (Severity level: 6 points)

The example begins: Suppose we are in real life, to judge whether a person A is bad; first of all we need to carefully observe his behavior, and then according to his multiple behaviors we conduct a comprehensive analysis, in order to accurately determine whether the character A is bad.
Assuming that the behavior of the character A coincides with the first item, that is, often gathering together with the bad people, it can only show that A has this behavior, but cannot determine A is bad, for it is possible A just played with friends, and did not do bad things. However, as A meets the first behavior item, A's behavior score is 5 points, and because the behavior score is not very high, A is judged as: normal ordinary people.
If A has other bad behaviors, such as behavior 2 (Severity level: 2 points), behavior 3 (Severity level: 30 points), then A's behavior score is: 5+2+30=37 points. A still cannot be considered to be bad, because A's current bad behavior is not very serious, but his behavior score is higher than the average person, so A is judged as: not very popular people.
Next, if A has other bad behaviors, such as behavior 4 (Severity level: 19 points), behavior 5 (Severity level: 7 points), behavior 7 (Severity level: 6 points), now A's behavior scores is: 37+19+7+6=69 points. At this time the score reaches 69 points which is a little high, but this value has not yet reached the critical value of being judged as a bad guy, so A is judged as: disgusted people who should be estranged.
If A has a lot of other bad behaviors, then his behavior score will continue to accumulate, and once the score exceeds a set value, then A will be judged as: a bad guy.
So far, you must have understood, right? This is the active defense strategy to determine based on "behavior" standard.
So according to this principle, you can consider an executable file as a "person", and then according to various acts of the "people" to comprehensively determine, whether the executable file is a normal file.
In the computer, there are a lot of behaviors that are not friendly. For example:
1. Intercept network data in the background of the operating system
2. Transfer the local data to a machine on the network without the user's consent or without the user's knowledge
3. Modify data of some normal software without permission
4. Collect the browser's personal privacy data
5. Pop up ads forcedly without the user's consent
6. Call some executable files that have been identified as viruses
7. Have frequent data communication with websites that have been proved to contain fraud, malicious behaviors.
8. Install the driver in the system to monitor a variety of data
... and other various unfriendly behaviors
By analyzing the code of an executable file, and establishing a virtual environment to simulate the operation of the executable file, in the course of the operation, the various bad behaviors will have accumulated scores. According to the final score, a file may be defined as one of the following types:
1. Normal file
2. File with suspicious behavior
3. Dangerous file with obvious malicious behavior
Why should the unknown file be uploaded to the server, and why not do a client for this function? How does the server analyze unknown files?
1. The server has a lot of data, as the data is too large, there is no way to integrate into the client.
2. The server will read all the code in the executable file into a virtual environment, then run the code of the executable file and rate the various actions of the file. This process requires a lot of hardware resources, while most of the personal computer configuration cannot meet this requirement.
I personally think that this "behavior-based" detection approach is a step forward, and a more secure solution that can deal with a variety of unknown new viruses.
I would like to share this idea, and wish computer security technical staff who read this, think about this direction.
Later, if I have a better idea, I will continue to share it, hoping to contribute to the cause of computer security, so that everyone is away from the computer virus, no longer suffering a variety of losses.
Why does the "T21" system apply the "behavior" based detection strategy, while also continuing to use the static signature method?
I said before, although the static signature cannot detect a new unknown virus, it has a very obvious advantage which is: fast detection speed at very low false detection rate, for the known virus file.
Therefore, the use of static signatures as an auxiliary detection approach can save a lot of time, but also reduce a lot of burden for the server.
Comment & Help
Copyright © 2016-2024 mygoodtools.com All rights reserved.